Maze Ransomware group has not slowed down even though much of the world has ground to a halt. One of Maze’s most recent targets was a wireless internet service provider in the USA. When Maze group is successful in locking and exfiltrating data from a company they post basic company info, lock date, and some of the stolen data as proof that they are not bluffing. According to a recent press release Maze waits 3-5 days with no company contact to post any information.
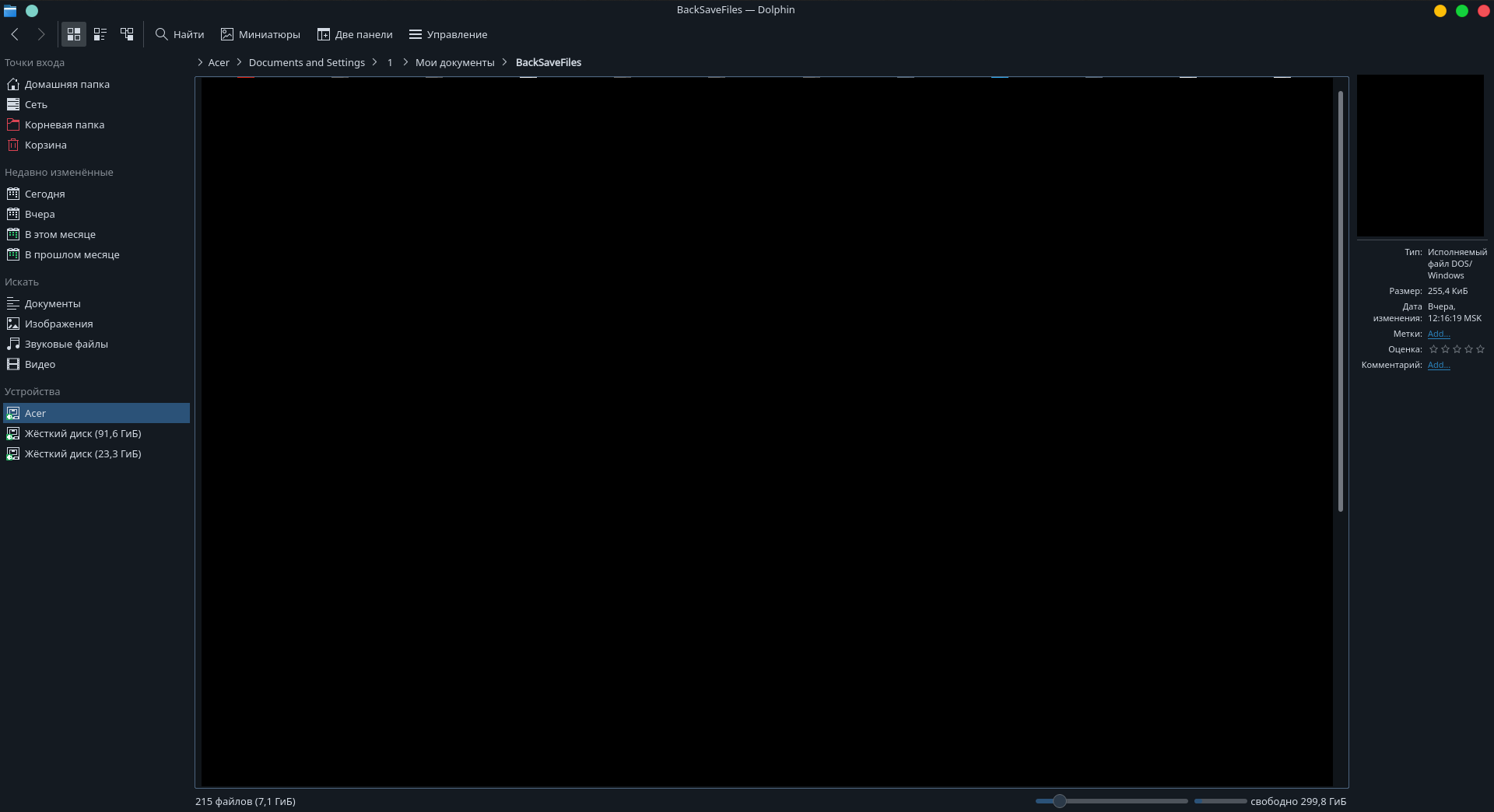
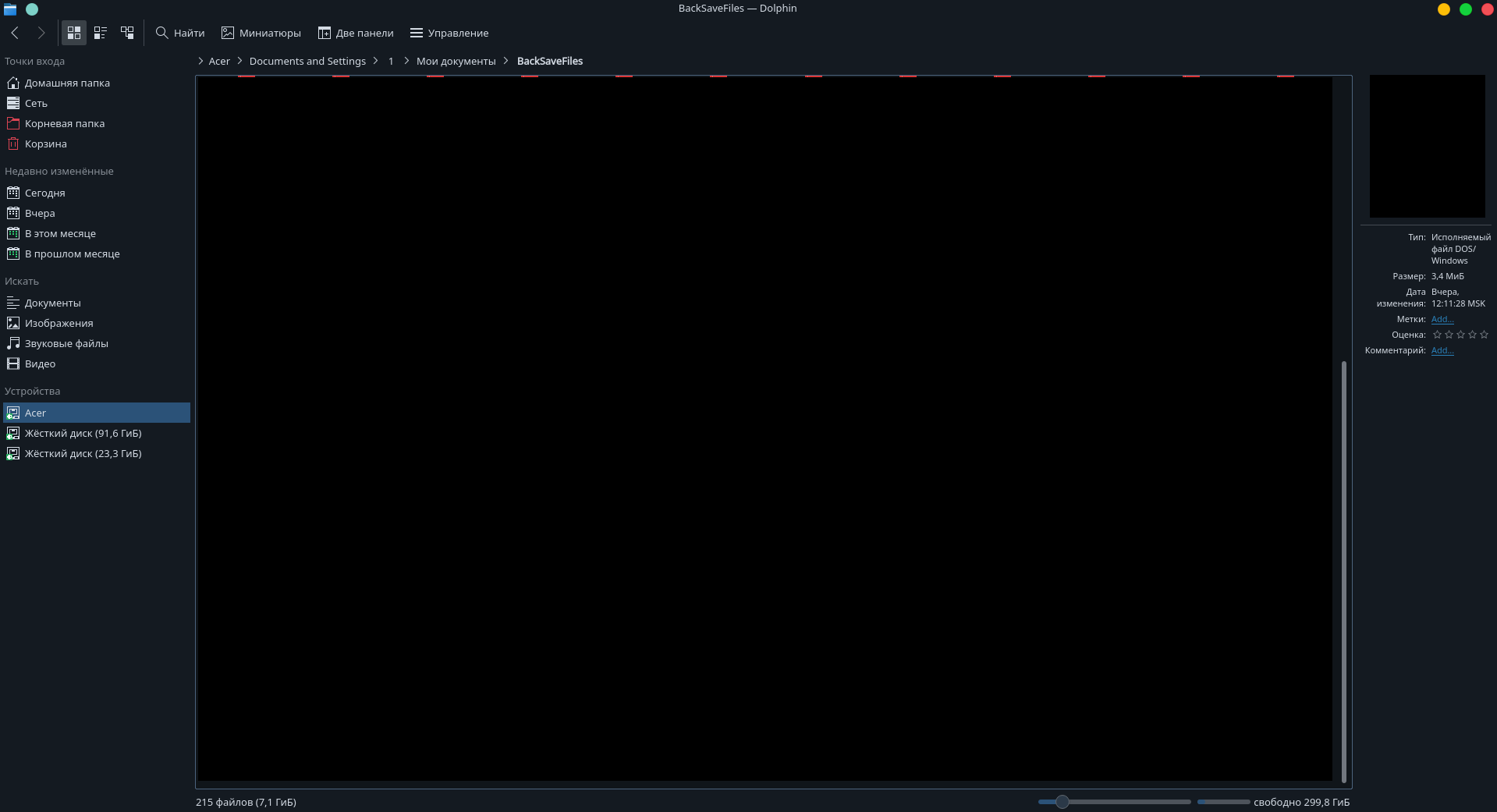
Usually the proof data is a few choice stolen files, but in this case all that was uploaded to Maze’s blog was two screenshots of a Linux file browser screen showing the names of some of the stolen files. I took a screenshot of both screenshots and redacted any file names.
McAfee’s analysis of code used in one of the Maze group’s attacks found that all of the command and control servers that were contacted by Maze’s ransomware were located in Russia. These screenshots seem to add more evidence that Maze group is operating out of Russia. Unless the OS language and time zone are set up to be intentionally misleading they are Russian and MSK (Moscow) respectively. The other non-proprietary information we can get from these screenshots was that the target was likely running an outdated OS, Windows XP. The folder that has been opened in the screenshot is “Acer > Documents and Settings > 1 > My Documents > Backsaves” – where the folder “Documents and Settings” is specific to Windows XP.
Another interesting thing that may point to a country of origin is the text of some of Maze’s “Press Releases”. Their latest release was about a multinational company that had become one of their “clients”. I don’t intend to enable Maze group so I’ve removed identifying information about their target but left the odd phrasing. I have colored sentences with missing or incorrect articles in purple.
Due to frequent inquires from various media about [COMPANY NAME] we decided to make a special press release.
The [COMPANY NAME is pretty larger: [COMPANY WEBSITE] . 5 major departments. [COMPANY DEPARTMENT NAMES]
Market capitalization of [TEN] billion and the profit of [HUNDREDS OF] millions according [BLOOMBERG ARTICLE]. Main activities in Real Estate, Construction and Telecomunications.
The company has offices in a few countries. We were contacted by [COUNTRY 1] and [COUNTRY 2] offices.
So lets examine the company. A few thousand millions of turnaround. A few thousands employees.
[COMPANY NAME] was attacked on [DATE]. The hole in the security perimeter was giant. It was so big that it was possible to download 200 Gb of private info in just 2 days. The was everything. Contracts, Clients, Employees Personal Data, Access credentials and much more interesting stuff.
In those 2 days company’s security didn’t even check the enormous activity inside the company’s network.
But despite of that, all the breaches inside the security perimeter are still open. That’s not because of COVID. It’s just the the laziness and absence of any will to do something.The company continues to live and work with the slogan «We have profit and it doesn’t matter who’s having psychologists us».
The negotiations are another funny story. It’s like a manual for business analytics and psychologists «How to ruin the negotiations».
It all begins with words of the scared employee of [COUNTRY 1] Office asking us What to do in such situation. It’s all ended with the words of the company’s president being insulted by the fact, some hackers have contacted personally his royal highness.
Dear mr. President. With your arrogance you have endangered not only your employees, but also your business partners. We have got access to some of your business partners through your network. And some of them will be attacked for sure.
Does it worth it to work with such «Giants». Does it worth investing at it? The company’s management doesn’t care about the company’s future. It doesn’t care about the data and about it’s business partners.
All we know is that the companies like [COMPANY NAME] will fail in the new economic reality.
We are going to make press releases about every large company that will try to escape the negotiations. So the companies’ investors will understand what company they are dealing with.
This is clearly not written by someone with English as their first language, but it also does not appear to my (totally unqualified) eye to have been automatically translated. Sentences leave out articles which is not unique to native speakers Slavic languages but certainly does not rule out Russia. According to Wikipedia the Russian language does not have definite, indefinite, numbered, gendered, or case-inflected articles. According to a native speaker of Ukrainian i spoke with, Russian speakers have trouble knowing which English articles to use and where.
Another seemingly relevant fact is that according to McAfee’s analysis none of Maze’s listed “clients” are Russian companies. If a non-Russian, Slavic language speaking country was carrying out these attacks I would think they would target Russian companies. Understanding the language and business practices of a target company are important for Maze’s bait to be enticing. Is this conclusive evidence that the Maze ransomware group is operating out of Russia? Maybe not, but it does add plausibility to the theory.
Maybe analysis of the other evidence files posted by Maze will reveal more clues about the group but I will leave that up to the professionals.